silverstripe / saml
Adds SSO/SAML authentication support to SilverStripe
Installs: 83 889
Dependents: 1
Suggesters: 0
Security: 0
Stars: 6
Watchers: 11
Forks: 29
Open Issues: 8
Type:silverstripe-vendormodule
Requires
- onelogin/php-saml: ^4.1.0
- silverstripe/framework: ^5
Requires (Dev)
- phpunit/phpunit: ^9.5
- squizlabs/php_codesniffer: ^3.0
Suggests
- silverstripe/ldap: Synchronise extra user attributes from Active Directory with LDAP
README
Table of Contents
Introduction
This Silverstripe module provides single sign-on authentication integration with a SAML provider.
This component can also be used alongside the default Silverstripe authentication scheme.
Requirements
- PHP 8+ with extensions: openssl, dom
- Silverstripe CMS 5 (see
2branch for Silverstripe 4) - Active Directory Federation Services 2.0 or greater (ADFS)
- HTTPS endpoint on Silverstripe site
- HTTPS endpoint on ADFS
This module has previously been tested on the following configurations, but is now untested:
- Windows Server 2008 R2 with ADFS 2.0
- Windows Server 2012 R2 with ADFS 3.0
Note: For LDAP only Active Directory integration, please see silverstripe-ldap.
Overview
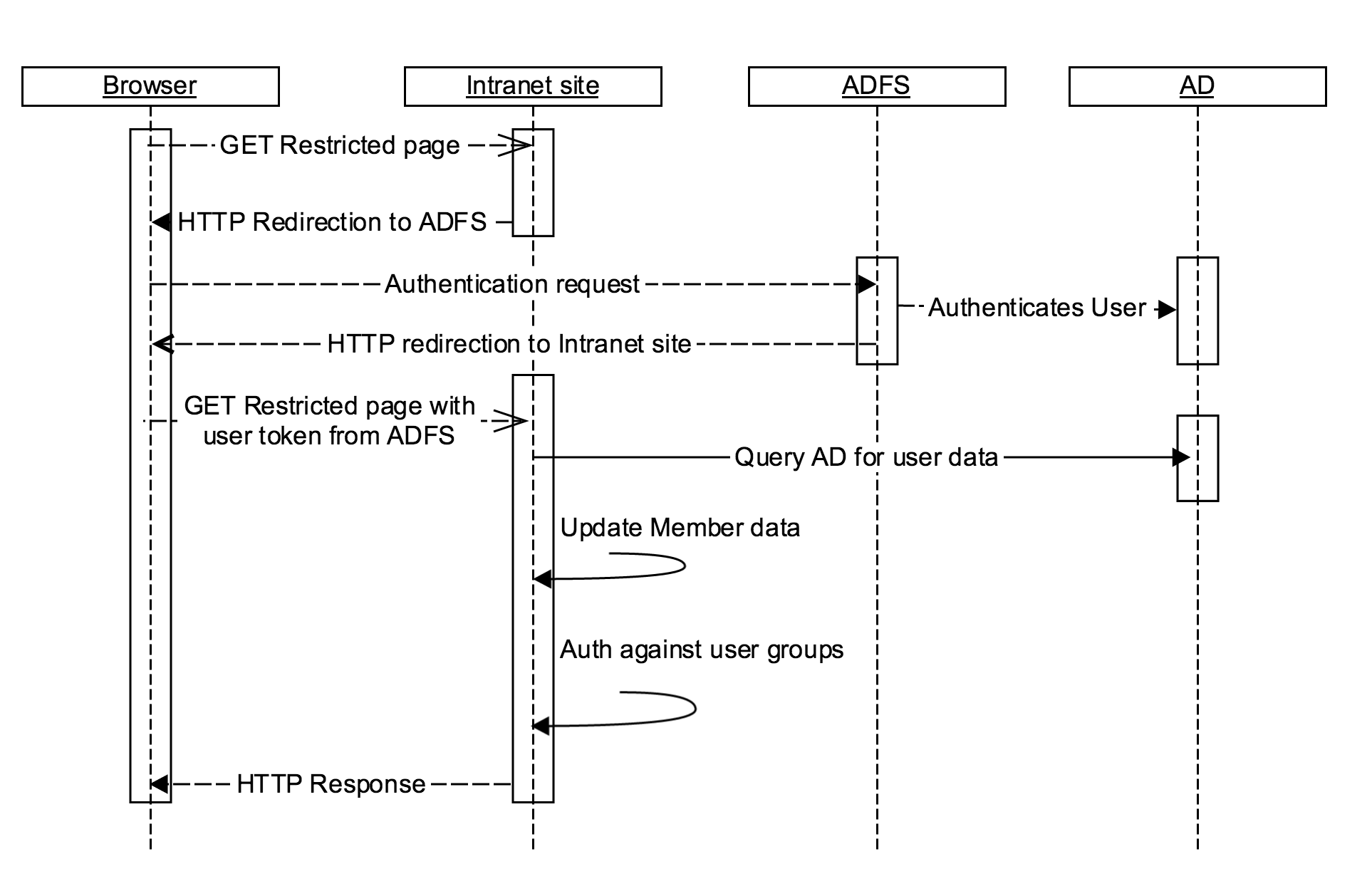 (Image) Typical authentication and authorisation flow for this module
(Image) Typical authentication and authorisation flow for this module
Security Assertion Markup Language (SAML) is an XML-based, open-standard data format for exchanging authentication and authorization data between parties. The single most important requirement that SAML addresses is web browser single sign-on (SSO).
With this module, Silverstripe site is able to act as a SAML Service Provider (SP) entity, and thus allows users to perform a single sign-on against a centralised user directory (an Identity Provider - IdP).
The intended counterparty for this module is the Active Directory Federation Services (ADFS). ADFS is a software component developed by Microsoft that can be installed on Windows Server operating systems to provide users with single sign-on access to systems and applications located across organizational boundaries.
ADFS uses a claims-based access control authorization model to maintain application security and implement federated identity. We rely on this mechanism for authentication, and for automated synchronisation of some basic personal details into Silverstripe.
This module doesn't allow you to store additional user attributes. If this is desired, you can optionally install the silverstripe-ldap module and run alongside to synchronise custom user attributes from an Active Directory server.
Security
With appropriate configuration, this module provides a secure means of authentication and authorisation.
For secure communication over the internet during the SAML authentication process, users must communicate with Silverstripe and ADFS using HTTPS. Similarly, for AD authentication to be secure users must access the Silverstripe site using HTTPS.
Silverstripe trusts ADFS responses based on pre-shared X509 certificates. These certificates are exchanged between the Identity Provider (ADFS) and the Service Provider (Silverstripe site) during the initial configuration phase.
In-depth guides
For Silverstripe developers
- Developer guide - configure your Silverstripe site
- Troubleshooting - common problems
For identity provider administrators
These guides will help you prepare your identity provider and configure it to work with the module correctly.
Changelog
Please see the GitHub releases for changes.
