yoeunes / regex-parser
A powerful PCRE regex parser with lexer, AST builder, validation, ReDoS analysis, and syntax highlighting. Zero dependencies, blazing fast, and production-ready.
Fund package maintenance!
yoeunes
Installs: 19 089
Dependents: 3
Suggesters: 0
Security: 0
Stars: 26
Watchers: 1
Forks: 3
Open Issues: 1
pkg:composer/yoeunes/regex-parser
Requires
- php: >=8.2
Suggests
- phpstan/extension-installer: To automatically enable the PHPStan rule for regex validation.
- phpstan/phpstan: To run static analysis and detect invalid regex patterns.
- psr/cache: To share AST cache via PSR-6 pools.
- psr/simple-cache: To share AST cache via PSR-16 caches.
- dev-main / 1.x-dev
- v1.3.0
- v1.2.0
- v1.1.0
- v1.0.10
- v1.0.9
- v1.0.8
- v1.0.7
- v1.0.6
- v1.0.5
- v1.0.4
- v1.0.3
- v1.0.2
- v1.0.1
- v1.0.0
- v1.0.0-RC1
- v0.31.0
- v0.30.0
- v0.29.0
- v0.28.0
- v0.27.0
- v0.26.0
- v0.25.2
- v0.25.1
- v0.25.0
- v0.24.0
- v0.23.0
- v0.22.0
- v0.21.0
- v0.20.0
- v0.19.0
- v0.18.0
- v0.17.4
- v0.17.3
- v0.17.2
- v0.17.1
- v0.17.0
- v0.16.0
- v0.15.1
- v0.15.0
- v0.14.13
- v0.14.12
- v0.14.11
- v0.14.10
- v0.14.9
- v0.14.8
- v0.14.7
- v0.14.6
- v0.14.5
- v0.14.4
- v0.14.3
- v0.14.2
- v0.14.1
- v0.14.0
- v0.13.0
- v0.12.0
- v0.11.0
- v0.10.0
- v0.9.0
- v0.8.0
- v0.7.0
- v0.6.0
- v0.5.1
- v0.5.0
- v0.4.0
- v0.3.0
- v0.2.0
- v0.1.10
- v0.1.9
- v0.1.8
- v0.1.7
- v0.1.6
- v0.1.5
- v0.1.4
- v0.1.3
- v0.1.2
- v0.1.1
- v0.1.0
This package is auto-updated.
Last update: 2026-01-22 19:38:38 UTC
README
RegexParser: Static Analysis, Linter & Logic Solver
RegexParser is a PHP 8.2+ library that treats regular expressions as code.
Unlike simple wrappers around preg_match, RegexParser implements a complete compiler pipeline (Lexer → Parser → AST) and an Automata-based Logic Solver (AST → NFA → DFA).
This architecture allows for advanced static analysis:
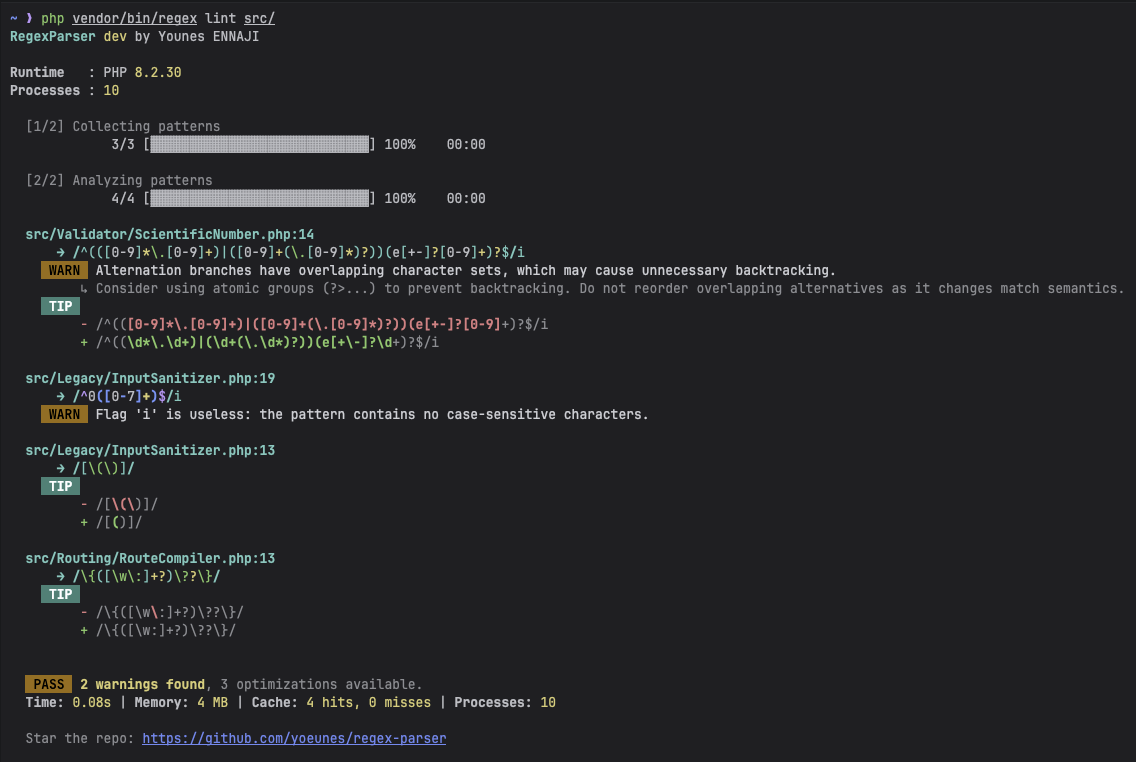
- Linting: Detect redundancy, useless flags, and optimizations.
- Safety: Statically detect catastrophic backtracking (ReDoS).
- Logic: Mathematically compare patterns (Intersection, Equivalence, Subset).
Built for learning, validation, and robust tooling in PHP projects.
If you are new to regex, start with the Regex Tutorial. If you want a short overview, see the Quick Start Guide.
Getting started
# Install the library composer require yoeunes/regex-parser # Try the CLI vendor/bin/regex explain '/\d{4}-\d{2}-\d{2}/'
What RegexParser provides
- 🏗️ Deep Parsing: Parse
/pattern/flagsinto a structured, typed AST. - 🧠 Logic Solver: Mathematically compare two regexes using NFA/DFA transformation. Detect route conflicts and validate security subsets.
- 🛡️ ReDoS Analysis: Analyze potential catastrophic backtracking risks structure-wise.
- 🧹 Linter: Clean up legacy code (useless flags, redundant groups) via the CLI.
- 📖 Explanation: Explain patterns in plain English.
- 🔧 Visitor API: A flexible API for building custom regex tooling.
Philosophy & Accuracy
RegexParser separates what it can guarantee from what is heuristic:
- Guaranteed: parsing, AST structure, error offsets, and syntax validation for the targeted PHP/PCRE version.
- Heuristic: ReDoS analysis is structural and conservative; treat it as potential risk unless confirmed.
- Context matters: PCRE version, JIT, and backtrack/recursion limits change practical impact.
How to report a vulnerability responsibly
If you believe a pattern is exploitable:
- Run confirmed mode and capture a bounded, reproducible PoC.
- Include the pattern, input lengths, timings, JIT setting, and PCRE limits.
- Verify impact in the real code path before filing a security issue.
See SECURITY.md for reporting channels.
Safer rewrites (verify behavior)
These techniques reduce backtracking but can change matching behavior. Always validate with tests.
/(a+)+$/ -> /a+$/ (semantics often preserved, but verify captures)
/(a+)+$/ -> /a++$/ (possessive, no backtracking)
/(a|aa)+/ -> /a+/ (only if alternation is redundant)
/(a|aa)+/ -> /(?>a|aa)+/ (atomic, avoids backtracking)
How it works
Regex::parse()splits the literal into pattern and flags.- The lexer produces a token stream.
- The parser builds an AST (
RegexNode). - Visitors walk the AST to validate, explain, analyze, or transform.
For the full architecture, see docs/ARCHITECTURE.md.
CLI quick tour
# Parse and validate a pattern vendor/bin/regex parse '/^hello world$/' # Get plain English explanation vendor/bin/regex explain '/\d{4}-\d{2}-\d{2}/' # Check for potential ReDoS risk (theoretical by default) vendor/bin/regex analyze '/(a+)+$/' # Colorize pattern for better readability vendor/bin/regex highlight '/\d+/' # Lint your entire codebase vendor/bin/regex lint src/
PHP API at a glance
use RegexParser\Regex; use RegexParser\ReDoS\ReDoSMode; $regex = Regex::create([ 'runtime_pcre_validation' => true, ]); // Parse a pattern into AST $ast = $regex->parse('/^hello world$/i'); // Validate pattern safety $result = $regex->validate('/(?<=test)foo/'); if (!$result->isValid()) { echo $result->getErrorMessage(); } // Check for ReDoS risk (theoretical by default) $analysis = $regex->redos('/(a+)+$/'); echo $analysis->severity->value; // 'critical', 'safe', etc. // Optional: attempt bounded confirmation $confirmed = $regex->redos('/(a+)+$/', mode: ReDoSMode::CONFIRMED); echo $confirmed->isConfirmed() ? 'confirmed' : 'theoretical'; // Get human-readable explanation echo $regex->explain('/\d{4}-\d{2}-\d{2}/');
Integrations
RegexParser integrates with common PHP tooling:
- Symfony bundle: docs/guides/cli.md
- PHPStan:
vendor/yoeunes/regex-parser/extension.neon - GitHub Actions:
vendor/bin/regex lintin your CI pipeline
Performance
RegexParser ships lightweight benchmark scripts in benchmarks/ to track parser, compiler, and formatter throughput.
- Run formatter benchmarks:
php benchmarks/benchmark_formatters.php - Run all benchmarks:
for file in benchmarks/benchmark_*.php; do echo "Running $file"; php "$file"; echo; done
Documentation
Start here:
Key references:
Contributing
Contributions are welcome! See CONTRIBUTING.md to get started.
# Set up development environment composer install # Run tests composer phpunit # Check code style composer phpcs # Run static analysis composer phpstan
License
Released under the MIT License.
Support
If you run into issues or have questions, please open an issue on GitHub: https://github.com/yoeunes/regex-parser/issues.