divineomega / laravel-password-exposed-validation-rule
Laravel validation rule that checks if a password has been exposed in a data breach
Fund package maintenance!
DivineOmega
Installs: 695 890
Dependents: 3
Suggesters: 0
Security: 0
Stars: 90
Watchers: 5
Forks: 41
Open Issues: 3
pkg:composer/divineomega/laravel-password-exposed-validation-rule
Requires
- php: ^7.1||^8.0||8.1
- illuminate/contracts: ^5.1||^6.0||^7.0||^8.0||^9.0
- jord-jd/password_exposed: ^5.0
Requires (Dev)
- php-coveralls/php-coveralls: ^2.0
- phpunit/phpunit: ^7.0||^8.0||^9.0
Replaces
README
This package provides a Laravel validation rule that checks if a password has been exposed in a data breach. It uses the haveibeenpwned.com passwords API via the jord-jd/password_exposed library.
Installation
To install, just run the following Composer command.
composer require jord-jd/laravel-password-exposed-validation-rule
Please note that this package requires Laravel 5.1 or above.
Usage
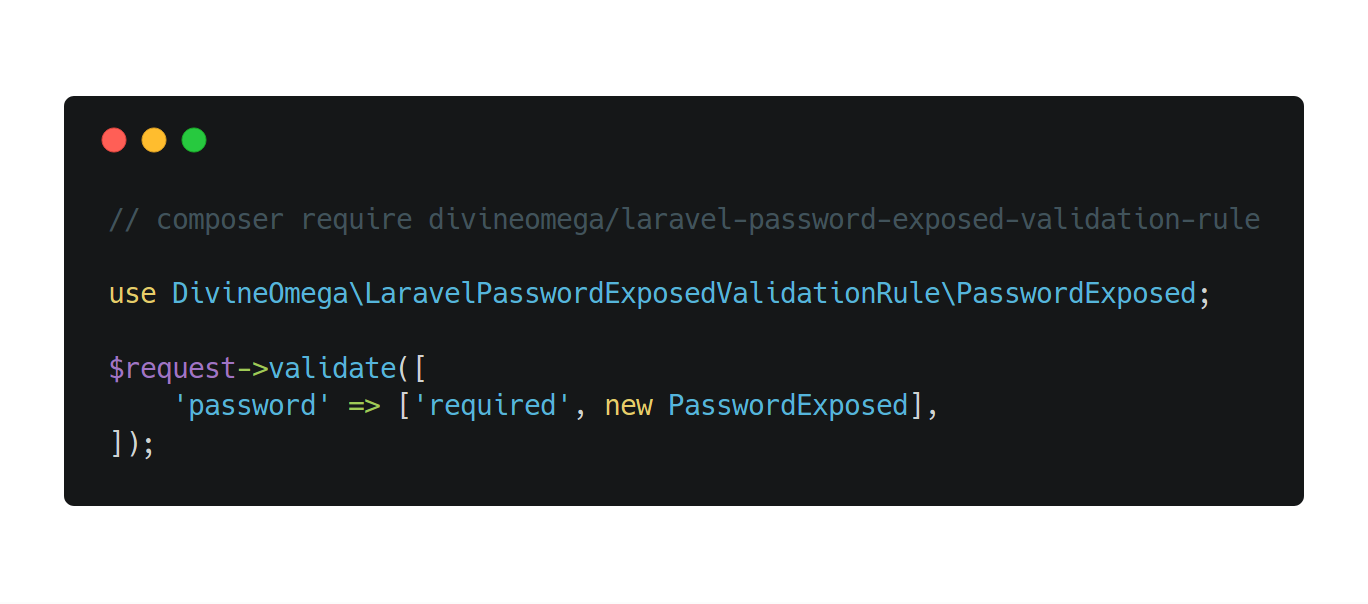
The following code snippet shows an example of how to use the password exposed validation rule.
use JordJD\LaravelPasswordExposedValidationRule\PasswordExposed; $request->validate([ 'password' => ['required', new PasswordExposed()], ]);
If you wish, you can also set a custom validation message, as shown below.
use JordJD\LaravelPasswordExposedValidationRule\PasswordExposed; $request->validate([ 'password' => ['required', (new PasswordExposed())->setMessage('This password is not secure.')], ]);